News - News In Brief
Worldwide scam campaign uncovered
December 22, 2021
.jpg) Advertisement
AdvertisementGroup-IB, one of the global cybersecurity leaders, has uncovered a worldwide scam campaign targeting users in over 90 countries all around the world, including the UAE, Oman, and Qatar. The fraudsters employ the tried and tested technique with fake surveys and giveaways purporting to be from popular brands to steal users’ personal and payment data, with the total number of big-name companies impersonated in the scheme exceeding 120. The new wave of the scam is particularly persistent thanks to an innovation in the scammers’ toolset — targeted links, which makes investigating and tackling such attacks increasingly challenging.
The potential victim pool of a single scam network is estimated at about 10 million people, while the potential damage totaled about $80 million per month, according to Group-IB’s Digital Risk Protection unit.
Personal customer service
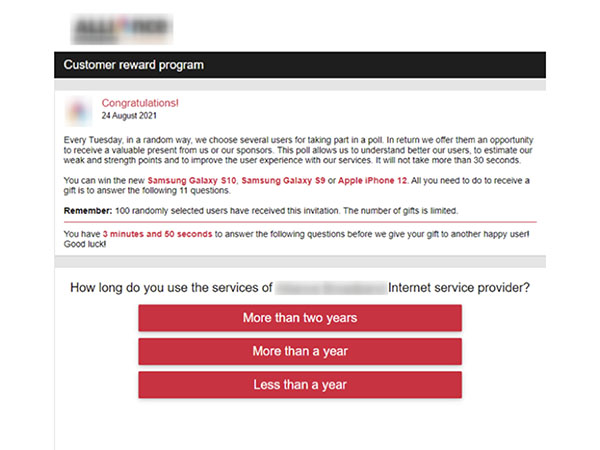
Fraudsters trap their victims by distributing invitations to partake in survey, after which the user would allegedly get a prize. Each such offer contains a link leading to the survey website. For “lead generation,” the threat actors use all possible legitimate digital marketing means: contextual advertising, advertising on legal and completely rogue sites, SMS, mailouts, and pop-up notifications. To build trust with their victims, scammers register look-alike domain names to the official ones. Less frequently, they were also seen adding links to the calendar and posts on social networks. After clicking the targeted link, a user gets in the so-called traffic cloaking, which enables cybercriminals to display different content to different users, based on certain user parameters.
But this destination “branded survey” page takes very long to download. This is because the victims find themselves in a long chain of redirects, during which scammers gather information about their session, including country, time zone, language, IP, browser, and etc. The content on the final page will be determined based on what was learned about the user and tailored as much as possible to their possible interests. The final scam link is customized to a specific user and can be opened only once. This complicates the detection of such links, which inevitably leads to the scam’s longer life cycle, and hampers the takedown and investigations.
At the final stage, the user is asked to answer questions to receive a prize from a well-known brand and to fill out a form asking for their personal data, which is allegedly needed to receive the prize. The data required usually includes the full name, email, postal address, phone number, bank card data, including expiration date and CVV.
An example of a scam page targeting English-speaking users
Fraudsters can use the data stolen to buy goods online, register fake user accounts on any online resources or simply sell the personal information on the dark web. Apart from revealing their data, users are sometimes asked to pay a tax or a test payment to receive the prize.
Scam’s scale: geography and victims
According to Group-IB DRP analysts, this type of fraud has been spotted in 91 countries, with cybercriminals exploiting at least 121 brands as bait. Based on the country of origin of the brands affected, the scam’s target regions are: Europe (36.3%), Africa (24.2%), and Asia (23.1%). In the Middle East alone, cybercriminals exploited 9 brands from Bahrain, Qatar, Oman, Kuwait and the UAE. Globally, cybercriminals mostly try to exploit the brands of leading telecommunications companies, which enjoy special “love” in this scheme, and make up more than 50% of the total number of brands exploited, followed by ecommerce and retail.
Group-IB analysts have detected at least 60 different scam networks that operate targeted links. On average, each of them contains over 70 domain names. One of the largest networks in terms of traffic attracted contained over 50 domain names. Judging from the number of visitors, scammers’ potential victim pool on this network alone totals 10 million people. Group-IB experts estimate the damage at $80 million per month, based on the number of sites detected, their minimum conversion, and an average money loss on a scam website. For each specific website that hosts fraudulent content, Group-IB team was able to analyze where the visitors came from. The main sources of traffic for targeted links operators are India (42.2%), Thailand (7%), and Indonesia (4.4%), among others.
“Just a couple of years ago, online scams were focused on scale: by indiscriminately targeting users, fraudsters tried to ensure that at least someone would take the bite,” comments Ashraf Koheil, Director of Business Development, Middle East & Africa at Group-IB. “Over time, as scam awareness was growing, fewer and fewer people fell prey to such scheme, which made it much more difficult for cybercriminals to make money. They started to explore new ways that would meet their financial ambitions. This triggered the scamdemic and the diversity of various fraudulent schemes that we observe today. The variety of scams observed globally today in described in detail in our annual Hi-Tech Crime Trends 2021/2022 report ‘Scams and Phishing’.”



.jpg)